⚫ Installed last available OpenWRT on AR750
login as: root
root@192.168.3.1's password:
BusyBox v1.35.0 (2023-04-27 20:28:15 UTC) built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt 22.03.5, r20134-5f15225c1e
-----------------------------------------------------
root@OpenWrt:~#
Source: [OpenWrt Wiki] GL.iNet GL-AR750
⚫ Expected configuration
One OpenWRT router getting internet access through a 4G USB dongle using NCM connection (much faster than PPP).
⚫ Configuration
⚪ Installing necessary packets on OpenWRT
# opkg update
# opkg installkmod-usb2 kmod-usb3 kmod-usb-net-huawei-cdc-ncm comgt-ncm kmod-usb-serial kmod-usb-serial-option kmod-usb-serial-wwan luci-proto-ncm usb-modeswitch kmod-usb-serial-ipw
# opkg install nano curl socat
Sources:
- Installer le firmware OpenWrt sur un routeur Wi-Fi
- Huawei E3272 и OpenWRT: klink0v — LiveJournal
⚪ Preparing the 4G USB dongle (Huawei E3272)
I bought for cheap money an old second-hand Huawei E3272. It was loaded with a HiLink software (22.X) and SIM locked.
It took me a day of struggle to sim unlock it and finally install a working stick software (21.X).
Sources:
Finally I installed a HiLink software + WEBUI to validate good working of the 4D USB dongle on Windows 10 then installed a stick software.
All downloaded from 3ginfo.ru :
- Huawei_E3272_Firmware_22.436.07.00.00_Universal_3Ginfo.ru.7z
- Huawei_E3272s_WebUI_17.100.08.00.03_general_3Ginfo.ru.7z
- Huawei_E3272s-153_Firmware_21.436.11.00.00_Universal_3Ginfo.ru.7z
All of this had to be done on a Windows 7 computer. Impossible to do on a Windows 10 computer.
⚫ Testing
⚪ Checking Huawei E3272 on OpenWRT
root@OpenWrt:~# socat - /dev/cdc-wdm0,crnl
AT
OK
AT^SYSINFOEX
^SYSINFOEX:2,3,0,1,,6,"LTE",101,"LTE"
OK
AT^SYSCFGEX=?
^SYSCFGEX: ("00","01","02","03","99"),((2000000400380,"GSM900/GSM1800/WCDMA900/WCDMA2100"),(4280000,"GSM850/GSM1900/WCDMA850"),(3fffffff,"All bands")),(0-2),(0-4),((c5,"LTE_B1/LTE_B3/LTE_B7/LTE_B8"),(7fffffffffffffff,"All bands"))
OK
ATI
Manufacturer: huawei
Model: E3272
Revision: 21.436.11.00.00
IMEI: XXXXXXXXXXXXXXX
+GCAP: +CGSM,+DS,+ES
OK
AT^FHVER
^FHVER:"E3272S-600 21.436.11.00.00,CH1E3272SM Ver.A"
OK
AT^VERSION?
^VERSION:BDT:Aug 30 2013, 12:47:28
^VERSION:EXTS:21.436.11.00.00
^VERSION:INTS:
^VERSION:EXTD:WEBUI_17.100.08.00.03_Hilink_V7R1_V3R2_V3R3
^VERSION:INTD:
^VERSION:EXTH:CH1E3272SM Ver.A
^VERSION:INTH:
^VERSION:EXTU:E3272
^VERSION:INTU:
^VERSION:CFG:1004
^VERSION:PRL:
OK
AT^SETPORT=?
^SETPORT:1: 3G MODEM
^SETPORT:2: 3G PCUI
^SETPORT:3: 3G DIAG
^SETPORT:5: 3G GPS
^SETPORT:A: BLUE TOOTH
^SETPORT:16: NCM
^SETPORT:A1: CDROM
^SETPORT:A2: SD
^SETPORT:10: 4G MODEM
^SETPORT:12: 4G PCUI
^SETPORT:13: 4G DIAG
^SETPORT:14: 4G GPS
OK
AT^SETPORT?
^SETPORT:A1,A2;10,12,16,A1,A2
OK
^Croot@OpenWrt:~#
root@OpenWrt:~#
root@OpenWrt:~#
⚪ Speed test
I made a speed test with PPP and NCM protocol to verify the common speech readable on internet:
NCM is definitly better performing.
⚪ USSD and SMS and Telegram
To be checked and tried:
Telegram
Send a message to telegram chat:
curl -X POST -H "Content-Type:multipart/form-data" -F chat_id=<CHAT_ID> -F text="message to test !!!" "https://api.telegram.org/bot<token_from_@BotFather>/sendMessage"
curl -s -X POST -H "Content-Type:multipart/form-data" -F chat_id=<CHAT_ID> -F text="message to test !!!" "https://api.telegram.org/bot<token_from_@BotFather>/sendMessage" | jq '.ok'
Get updates from telegram chats:
curl -s https://api.telegram.org/bot<token_from_@BotFather>/getUpdates | jq
curl -s https://api.telegram.org/bot<token_from_@BotFather>/getUpdates | jq '.result[].message.text'
curl -s https://api.telegram.org/bot<token_from_@BotFather>/getUpdates | jq '.result[].message.date'
Send a message+file to telegram chat:
curl -s -X POST https://api.telegram.org/bot<token_from_@BotFather>/sendDocument -F chat_id=<CHAT_ID> -F document=@'/path/to/document' -F caption='your message here'
Receive SMS with smstools3 and forward to Telegram
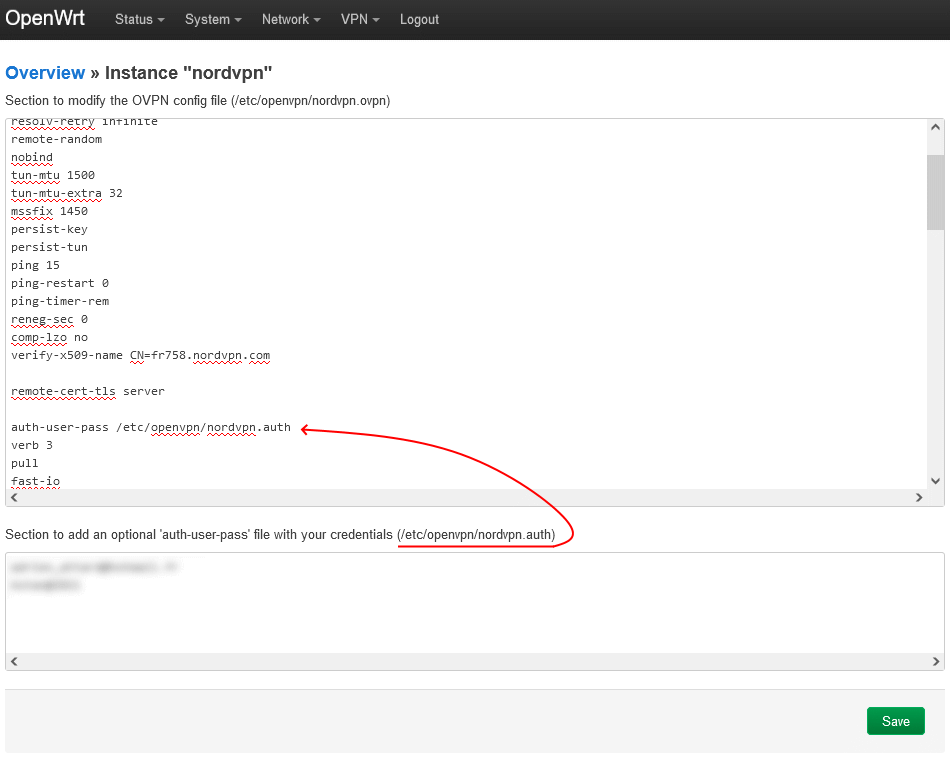
opkg install kmod-usb-serial kmod-usb-serial-wwan kmod-usb-serial-option usb-modeswitch smstools3 curl iconv jq bc
mkdir /usr/local
mkdir /usr/local/bin
nano /usr/local/bin/pushsms
This file will be called as soon as a new SMS is received in order to transfer it to a Telegram chat:
#!/bin/sh
# /usr/local/bin/pushsms
# chmod +x /usr/local/bin/pushsms
chat_id=<CHAT_ID>
token=<token_from_@BotFather>
if [ "$1" == "RECEIVED" ] || [ "$1" == "REPORT" ]; then
from=`grep "From:" $2 | awk -F ': ' '{printf $2}'`
#sent=`grep "Sent:" $2 | awk -F ': ' '{printf $2}'`
#received=`grep "Received:" $2 | awk -F ': ' '{printf $2}'`
alphabet=`grep "Alphabet:" $2 | awk -F ': ' '{printf $2}'`
if [ "$alphabet" = "UCS2" ]; then
content=$(sed -e '1,/^$/ d' < "$2" | iconv -f UNICODEBIG -t UTF-8)
else
content=$(sed -e '1,/^$/ d' < "$2" | iconv -f "windows-1252" -t UTF-8)
fi
text=$(cat << EOF
$content
From $from
EOF
)
curl -s -d "chat_id=$chat_id&text=$text&disable_web_page_preview=true" -X POST https://api.telegram.org/bot"$token"/sendMessage
fi
Don't forget to make above file executable.
Now editing the configuration of smstools3:
# /etc/smsd.conf
#
# Description: Main configuration file for the smsd
#
devices = GSM1
incoming = /var/spool/sms/incoming
outgoing = /var/spool/sms/outgoing
checked = /var/spool/sms/checked
failed = /var/spool/sms/failed
sent = /var/spool/sms/sent
receive_before_send = no
autosplit = 3
logfile = 1
loglevel = 5
eventhandler = /usr/local/bin/pushsms
# Uncomment (and edit) this section to allow smsd to start:
#
[GSM1]
init = AT+CPMS="ME","ME","ME"
device = /dev/cdc-wdm0
incoming = yes
#pin = 0000
baudrate = 9600
signal_quality_ber_ignore = yes
detect_unexpected_input = no
memory_start = 0
cs_convert_optical = no
report = yes
Now restart the utility:
/etc/init.d/smstools3 restart
And check logs:
logread | grep smsd
Send SMS with smstools3
sendsms 491721234567 'Hello, how are you'
Some method to send USSD code from command line
root@OpenWrt:~# socat - /dev/cdc-wdm0,crnl
AT+CUSD=1,"AA18CC3602",15
OK
^MODE: 5,4
^RSSI: 26
+CUSD: 0,"041204300448002004370430043F0440043E044100200432002004340435043B04350020003A002900200421043A043E0440043E0020043F04400438043B043504420438044200200053004D00530020043E00200432044B043F043E043B043D0435043D043804380021",72
OK
^Croot@OpenWrt:~#
Open kinda serial communication link with modem:
root@OpenWrt:~# socat - /dev/cdc-wdm0 << EOF
> AT+CUSD=1,"AA18CC3602",15
> EOF
OK
root@OpenWrt:~#
root@OpenWrt:~# cat /dev/cdc-wdm0 | grep +CUSD: > ./USSDresult.txt &
root@OpenWrt:~# echo -e -n "AT+CUSD=1,\"AA18CC3602\",15\r\n" > /dev/cdc-wdm0
root@OpenWrt:~# killall cat
[1]+ Done cat /dev/cdc-wdm0 | grep +CUSD: 1>./USSDresult.txt
root@OpenWrt:~# cat ./USSDresult.txt
+CUSD: 0,"041204300448002004370430043F0440043E044100200432002004340435043B04350020003A002900200421043A043E0440043E0020043F04400438043B043504420438044200200053004D00530020043E00200432044B043F043E043B043D0435043D043804380021",72
root@OpenWrt:~# cat ./USSDresult.txt | sed -e 's@+CUSD: 0,"@@g;s@",15@@g;s@",72@@g'
041204300448002004370430043F0440043E044100200432002004340435043B04350020003A002900200421043A043E0440043E0020043F04400438043B043504420438044200200053004D00530020043E00200432044B043F043E043B043D0435043D043804380021
root@OpenWrt:~# rm ./USSDresult.txt
root@OpenWrt:~#
To code the USSD code and decode the answer you can use this tool: SMSTools3 PDU Converter. Or these two first shell script functions below. Third function to code USSD, catch the answer and decode it:
#!/bin/sh
# Idea: https://github.com/Shumaher/huawei-ussd/blob/master/ussd.sh
# But slightly modified to make it work
decodeUCS2() # UCS2 to text (to decode USSD answer)
{
bytes=$(echo -n $1 | sed "s/\(.\{2\}\)/\\\x\1/g")
REPLY=$(printf $bytes | iconv -f UNICODEBIG -t UTF-8)
echo -n "$REPLY"
}
encodePDU() # text to PDU (to code the USSD)
{
in=$1
let "in_len=${#in}-1"
for chr in $(seq 0 $in_len)
do
let "chr2=$chr+1"
let "t=$chr%8+1"
if [ "$t" -ne 8 ]; then
byte=$(printf "%d" "'${in:$chr:1}")
let "c=$byte>>($chr%8)"
let "c2=(1<<$t)-1"
byte2=$(printf "%d" "'${in:$chr2:1}")
let "b=$byte2 & $c2"
let "c=$b<<(8-$t) | $c"
REPLY=$REPLY$(echo "obase=16; $c" | bc | sed 's/\<[0-9A-F]\>/0&/' )
fi
done
# echo "AT-command to send '$1' as USSD-request: 'AT+CUSD=1,\"$REPLY\",15"
echo -n "$REPLY"
}
sendUSSD() # To send an USSD code to operator and get result
{
ussd_human=$1
ussd_pdu=$(encodePDU $ussd_human)
rm -f ./USSDresult.txt
cat /dev/cdc-wdm0 | grep "+CUSD: 0," > ./USSDresult.txt &
echo -e -n "AT+CUSD=1,\"$ussd_pdu\",15\r\n" > /dev/cdc-wdm0
# wait up to 10 seconds for the answer
sleeptime=10
while [ $(cat ./USSDresult.txt | grep -c "+CUSD: 0,") -le 0 ] && [ $sleeptime -ge 1 ]
do
sleep 1
sleeptime=$(($sleeptime - 1))
done
killall cat
# here could add an 'if' statement in case 10sec waited and answer still not catched
REPLY=$(cat ./USSDresult.txt | sed -e 's@+CUSD: 0,"@@g;s@",15@@g;s@",72@@g' | tr -d '\r\n')
REPLY=$(decodeUCS2 "$REPLY")
echo -n "$REPLY"
rm ./USSDresult.txt
}
=> sendUSSDcatchANSWER.sh
Various sources: